Permissions
You will require an Access Role with the following permissions:
- Single Sign-On
- Initial Configuration Required - Contact your Account Manager
Step 1 - Access Role Setup
In order for a user to be able to view and have access to the Single Sign-On menu in Assure Expenses, it must be licenced for your company and the correct Access Role and permission assigned.
- Navigate to from the homepage to Administrative Settings | User Management | Access Roles. You can then either create a new Access Role specifically for the SSO users or edit an existing role by clicking
 adjacent to the Access Role name.
adjacent to the Access Role name. - Under the 'System Options' subheading is the Single Sign-On element. Select the checkbox to provide the assigned users with all of the permissions that they require to use the functionality within the Single Sign-on menu.
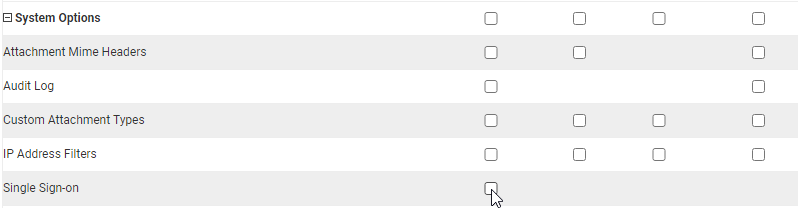
- Click save at the bottom of the page to store the changes.
Note: The Single Sign-on Access Role permission will only show if it has been activated for your organisation by RLDatix. You will need to contact your RLDatix Account Manager (accountmanagers@selenity.com) to purchase SSO or raise a ticket with our service desk if you believe this should be available.
Note: The Access Role must be assigned to the user/s that you want to have this functionality. For more information, view Add an Access Role to an Employee.
Step 2 - Configure SSO Settings
You will now need to start configuring the SSO settings within Assure Expenses. Navigate from the homepage to Administrative Settings | System Options | Single Sign-on. Each of the options listed on this page are described below:
Note: If you cannot see this menu option, please refer to Step 1 - Access Role Setup.
Service Provider (RLDatix)
The information in this panel is provided by RLDatix. This will need to be entered into your Identity Provider during configuration.
| Option | Description |
|---|---|
| SAML Version | This displays the version of SAML (Security Assertion Markup Language) which is supported by RLDatix. |
| SSO service URL | Provided by RLDatix. This is the URL to which your Identity Provider needs to direct requests to log on. This address will always begin https:// using the encrypted protocol for secure communication over the internet. |
| Expenses Public Certificate | Your SAML properties must be encrypted using this certificate. This is recommended for security. Click Download to start downloading the Assure Expenses Public Certificate. |
Identity Provider
The information below is taken from your Identity Provider and needs to be entered here to configure SSO within Assure Expenses. See Single Sign-On (SSO) - Feature Overview for more information on Identity Providers.
| Option | Description |
|---|---|
| Issuer | This is the unique identifier of the Identity Provider, which will be sent in the <saml:issuer> element of the SAML Assertion. |
| Identity Provider Public Certificate | This is the counterpart to the Private Key used to sign the SAML Assertion. This is an export of your token-signing certificate from your Identity Provider. This must be an X.509 certificate as a .cer file. Click Choose File which will allow you to browse your computer/network for the Identity Provider Public Certificate. Click Change to update an expired certificate. |
SAML Request
The information that is entered into the fields below will determine how a user within your organisation will be identified. This information tells RLDatix how to identify the user from the SAML assertion received from you.
When a user wants to log into Assure Expenses using SSO, a SAML assertion is sent to Assure Expenses.
Example:
company=”example_company” email=”myemail@example_company.com”
The SAML Assertion needs to contain:
| Option | Description |
|---|---|
| Company ID (who the user works for) | When you logon to Assure Expenses to configure this page you need to enter the 'companyid' as part of your credentials. This will be displayed on this form. Set this value in your Identity Provider configuration exactly as it is shown within the product. This is sent as part of the SAML Assertion (case sensitive). |
| Company Identifier Attribute | This is the name that you use to identify the field that contains the company ID field value. Most leave this as the name “company”. |
| Identifier Attribute (the information used to identify the individual user) | The user’s unique identifier (e.g. Username or Email Address) must be sent as part of the <saml:AttributeStatement>; this is the name of that attribute. Most use either “email” or “user”. In the SAML this will then be followed by the identifier of the person to logon (e.g. email address or username) as specified in the lookup field below. |
| Identifier Lookup Field | This specifies the field name in Assure Expenses that is searched to identify the user. For example, if your identity provider is passing over the email address of the user then choose “email address”. Select the field you would like the unique identifier to be. This will be sent in your SAML Assertion.
|
Redirection
For instances when a user cannot login, you are able to create specific intranet pages which provide the user with further information which is specific to your organisation. The URLs for these pages should be entered in the fields below.
| Option | Description |
|---|---|
| Login Error URL | If specified, any attempt to logon with invalid details will be redirected to this URL e.g. a user who has not yet been set up within Assure Expenses. It would be considered best practice to provide useful information to help the user if they are directed to this page. |
| Session timeout URL | If specified, when a user is inactive and their logon session expires, they will be sent to this URL. |
| Exit URL | If specified, when a user exits they will be sent to this URL. |
 adjacent to the Access Role name.
adjacent to the Access Role name.
